F5 on GCP
Some Roles your gmail identity (or cloud identity) may need on GCP for successfully creating Terraform Resources
It is best to create a custom role in GCP. Assign your human user (gSuite identity) this custom role and use that as the default credential, when you connect from your local development machine (i.e. your custom service account credentials should be commented out, so TF can use the Application Default Credentials - human credentials - instead).
provider "google" {
//credentials = file("account.json")
project = "my-awesome-f5"
region = "us-central1"
zone = "us-central1-c"
}
- iam.serviceAccounts.actAs permission for your project - e.g. 'projects/my-awesome-project'
- If you plan to use the default compute engine SA, you would need to be granted the role - serviceAccountUser for that SA. Ask a project owner to grant you the iam.serviceAccountUser role on the service account
- If you will be creating your own SAs and assigning roles to them,
- resourcemanager.projects.getIamPolicy on the my-awesome-project
- resourcemanager.projects.setIamPolicy on the same project
- iam.roles.list - on the same project.
What is F5 BigIP? What are the different configurations?
Big IP means a SINGLE VIRTUAL IP presented as the front of a load balancer for all the backend instances.
It can be configured to run in 3 different modes - based on the number of IP addresses allocated to the device.
Single NIC vs. Dual NIC vs. Triple NIC
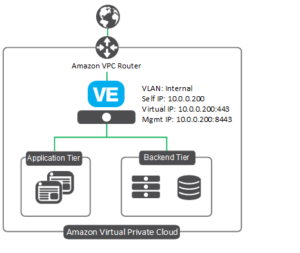
What are some of the gotchas in spinning up the F5 BigIP Instance through the marketplace?
From your end customer, there are a few things you need to try and figure out up front:
- How will admins access the Compute Instance ? (SSH is usually the best option, but there's a couple of nuances here as well. Admins can also access the instances directly via gCloud and the Console).
- How will IP addresses be assigned to the instance? By default, ephemeral IPs are assigned - which are lost on restart.
- Is VM IP Forwarding allowed (okayed) by your customer's security team?
- Is storing SSH keys in the instance metadata allowed?
Accessing the F5 instance via SSH (SSH Keys in Compute Engine Instance metadata )
Option 1 - Enable OS Login. OS Login uses IAM roles to provide your public SSH key to the instance through your Google Account or a managed user account.
When setting up OS Login, ensure that you have first added the SSH keys to a user account (i.e. added your public key to the user account that you want to use to connect to your VM).
Option 2 a (Instance Metadata) - Manually add and remove SSH keys by editing project or instance metadata. This method adds a little risk and is typically NOT recommended unless the OS Login method above does not work for you. However, a significant advantage of this method is that it works for ALL users (since the keys are stored at an instance level). It might be ideal for a DEVELOPMENT environment, where multiple users need access to the F5 instance.
Option 2 b (Project Metadata) - Same as 2a , except the SSH key is applied to the project metadata. It is applicable to ALL instances in the project (even riskier than 2a).
Option 3 - SSH Keys Managed for you
-- You can also connect to instances through the Google Cloud Console, where Compute Engine automatically manages the full lifecycle of your keys, or
Option 4 - SSH Keys via gCloud
Using the gcloud command-line tool in the SDK, where Compute Engine configures persistent SSH key metadata for you.
Enable IP Forwarding
In order to get the traffic forwarded from the F5 instance to the backend pool, you will need to enable IP forwarding on the instance, once it is up and running,
- Go into the Networking menu for the F5 instance.
- Select a network interface by clicking the edit button. Since this was a single NIC install, there should be only one Network Interface associated with this instance.
- For the network interface, choose On from the IP forwarding
Where do I cofigure the backends?
BigIP has a configuration Utility that is accessible via your F5's ephemeral IP . This is where you would do the initia. setup of your app pool (backend for F5). Look for the Pools Option and the Health Monitor option on this UI.
LTM - Local Traffic Manger --> Pools --> Health Monitor
What ports do I need to open for my backend?
Outbound - You will need to allow traffic on 443 outbound (this is allowed by default on GCP Compute Instances, so you should not need to tweak anything here).
Inbound - You will need to allow inbound 443 traffic on the backend App Servers (e.g. Web Server, NGINX Instance etc.).
What does a failed health monitor indicate? And how does one troubleshoot it?
A failing health check may indicate that a health monitor is marking a pool, pool member, or node as indefinitely down or that a monitor is repeatedly marking a pool member or node as down and then as back up (often called "bouncing").
For example, if a misconfigured health monitor repeatedly marks pool members as down and then as back up, connections to the virtual server may be interrupted or fail altogether. If this occurs, you need to determine whether the monitor is misconfigured, the device or application is failing, or some other factor, such as a network-related issue, is causing the monitor to fail. The troubleshooting steps you take depend on the monitor type and the symptoms you observe.
What is the approximate cost of F5 on GCP?
There are two parts to the cost - one is the actual license plus 'usage' fee (fixed monthly fee). The other is the resource consumption for the Compute Instance fee (shown in the table below).
F5 BIG-IP Virtual Edition - GOOD - BYOL - $50/mo PLUS BYOL fee
F5 BIG-IP Virtual Edition - BETTER - BYOL - $100/mo
| Item | Estimated costs |
|---|---|
|
F5 BIG-IP Virtual Edition BYOL - All Modules - 2 Boot Locations usage fee (BYOL)
Google does not collect this license fee.
|
Varies |
| Google Compute Engine Costs | |
| VM instance: 4 vCPUs + 15 GB memory (n1-standard-4) | $138.70/month |
| Standard Persistent Disk: 82GB | $3.94/month |
| Sustained use discount | − $41.61/month |
| Total | $101.03/month + BYOL license fee |
Logging into the OS
ssh -i PATH_TO_PRIVATE_KEY gSuiteUserId@EXTERNAL_IP
Common Issues and Troubleshooting F5 BigIP on GCP
Logging into the Management GUI of F5 bigIP
- https://GCP-External-IP:8443/tmui/login.jsp
Default Creds - admin / admin - will not work.
You need to change the admin password using these steps
TIP: To SSH into your instance, use putty - and your own key pair (hopefully, that's what you used to associate with the instance). Using default SSH access that GCP controls and provides, did not work. Once SSH'ed in, do the following:
- modify auth password admin
Press Enter. The terminal screen displays the message: - changing password for admin
- new password:
confirm password - save sys config - IMPORTANT
Once you login to F5, you need to
- a) Enter and Activate the license key (this needs to be done periodically, even with a valid license)
- b) Once activated, F5 will show as 'Running/Active' (as opposed to 'offline'). Now, you should see a full menu (on the left side). System menu will let you add modules (e.g. Advanced Policy Manager APM, Advanced Firewall Manager AFM...)
- c) You can also configure the STANDALONE vs. HA mode. This is F5 NATIVE HA Mode - as opposed to HA provided by the instance group resource in GCP/AWS/Azure.
Part 2 of this F5 on GCP post will deal with some advanced scenarios, including:
- High Availability Configuration
- Can you use GCP Auto Scaling with F5? What about Target Groups?
- Can the target groups be Cloud Functions?
- What about DNS? How is that handled?
- How many Network Interfaces Needed for F5 Appliances ?
- How many IP Addresses are needed for F5?
- Attaching multiple network interfaces to an F5 BigIP instance
- How do I install F5 on GCP through Terraform?
Summary
There are a few questions one needs to answer before setting out on an F5 on GCP install. This post summarizes some of the common issues you might encounter.
Need Assistance? Set up a free 30 minute consultation.
Leave a Reply