More on VPC Service Controls…
Also read Service Accounts in GCP and VPC Service Controls - 2 minute GCP Security Solution
- Protects against theft of OAuth Credentials or Service Account credentials.
- Network egress control - If an IAM user within the perimeter is malicious, they still cannot alter / access any GCP resource outside the perimeter
VPC Service Control Perimeter around a Public API? Can I restrict the API to be only called from specific IP Addresses?
Yes = even though the API is publicly accessible, you can restrict the client IPs that can call the API. This is because the API resource exists within your PROJECT - and you control who or what gets into this project.
Service Account IP Restriction - Defining an access level and a Perimeter
A new access Level can be created. This access level can be a SUBNETWORK (CIDR block of private or public IPs.) The Public IPs would be the NAT'ed IP of the client that was invoking the GCP Service.
When we define the service control perimeter, we PICK (from an access control dropdown) the specific access level that we created in step 1.
Note that the Service Control is defined at the Org Level (and requires you to be an Organizational Admin). However, it is actually implemented at the PROJECT level - the very first thing you have to do is PICK The projects you are trying to protect.
What if I need to access the resources from Cloud Shell?
Cloud Shell exists OUTSIDE your project - so it will be locked out of a regular perimeter that is based on a CIDR subnetwork access-level. However, there is a way to add an INGRESS exception that is based on user identities. That ingress is based on your Cloud IAM identity - and can allow you in as a console user.
From the Cloud Shell tab, create an ingress policy that allows your user identity to ingress to the Compute Engine service only, and apply the policy to your perimeter.
cat <<EOF > ingress_spec.yaml
- ingressFrom:
identities:
- user:$USERNAME
sources:
- accessLevel: '*'
ingressTo:
operations:
- methodSelectors:
- method: '*'
serviceName: compute.googleapis.com
resources:
- '*'
EOF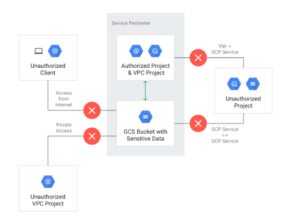
Summary
VPC service controls are an easy way to do defense in depth security around your GCP assets.
Leave a Reply