Accessing Google APIs – clarifying Authentication and Authorization for Web and Mobile Apps
Mobile Apps can use either OAuth 2.0 (described below) or Google Sign-in for Android or iOS.
Web Apps and Desktop Apps should try and use OAuth 2.0 as described in this post.
Mobile Application Authorization Scenarios - Using OAuth 2.0 for Accessing Google APIs - Mobile (iOs , Android) or Windows Desktop Apps
Google Supports common OAuth 2.0 scenarios such as those for web server, client-side, installed, and limited-input device applications.
General OAuth Flow for Google APIs
OAuth can be used for both - authentication and authorization. OAuth 2.0 client credentials can be created from the Google API Console. All Authorization Requests go to the Google Auth Server. For Authentication requests, follow Open ID Connect Guidelines.
Once your client credentials are created (Google authorization server now has a record of what these are), client application requests an access token from the Google Authorization Server --> extracts a token from the response --> sends the token to the Google API that you want to access. For these authentication scenarios (Web Apps, Desktop Apps, Mobile Apps), follow the steps in this google doc
Web Application Authorization Scenarios - Using OAuth 2.0 for Accessing Google APIs - Web Apps
Step 1 - Open the API Library in your cloud console
https://console.cloud.google.com/apis/library?project=myproject
Step 2 - Consent Screen for OAuth.
This requires you to know the app domain and the redirect URI. The redirect URI is where the google authorization server will send a successfully authorized user. Per their documentation:
A redirect URI, or reply URL, is the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token.
Step 3 - Creating authorization credentials for your web application
Note - There are three different type of OAuth Credentials. For our purposes (Web App, Mobile Apps, Desktop Apps, Windows, MAcOS..) , we need the second option (OAuth Client 2.0 credentials)
Any application that uses OAuth 2.0 to access Google APIs must have authorization credentials that identify the application to Google's OAuth 2.0 server. The following steps explain how to create credentials for your project. Your applications can then use the credentials to access APIs that you have enabled for that project.
- Go to the Credentials page.
- Click Create credentials > OAuth client ID (the second option above).
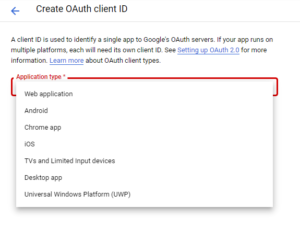
- Select the Web application application type.
- Fill in the form and click Create. Applications that use languages and frameworks like PHP, Java, Python, Ruby, and .NET must specify authorized redirect URIs. The redirect URIs are the endpoints to which the OAuth 2.0 server can send responses. These endpoints must adhere to Google’s validation rules.
For testing, you can specify URIs that refer to the local machine, such as http://localhost:8080. With that in mind, please note that all of the examples in this document use http://localhost:8080 as the redirect URI.
We recommend that you design your app's auth endpoints so that your application does not expose authorization codes to other resources on the page.
After creating your credentials, download the client_secret.json file from the API Console. Securely store the file in a location that only your application can access.
Authentication Scenarios
Use openID connect
Leave a Reply