East to West Traffic Filtering using Palo Alto on GCP
Set up a 1 on 1 appointment with Anuj to assist with your cloud journey.
First, you will need to decide whether egress, ingress or BOTH types of traffic are in need of palo alto based traffic inspection.
Some Definitions - Applicable to both AWS and GCP
-
Inbound traffic—traffic originating outside the VPC and destined to resources within your application VPC, such as web servers. VM-Series firewalls prevent malware and vulnerabilities from entering the network in traffic allowed by GCP Firewall Rules or AWS security groups.
-
Outbound traffic—traffic originating within the application VPCs and destined to external resources on the Internet. The VM-Series firewalls protect outbound traffic flows by ensuring that workloads in application VPCs connect to permitted services (such as Windows Update) and allowed URL categories and preventing data exfiltration of sensitive information. Additionally, VM-Series security profiles prevent malware and vulnerabilities from entering the network in the return traffic.
-
East-West traffic—in a transit gateway environment (AWS) or Shared VPC Environment (GCP), East-West traffic refers to Inter-VPC traffic, such as the traffic between source and destination workloads in two different application VPCs. The VM-Series firewalls protect east-west traffic flows against malware propagation.
Egress Traffic Inspection? Traffic Going to the data center?
Anything going to the data center should be inspected through a Palo Alto Appliance!
Where will PA be situated?
Palo alto sitting in a public subnet (on a transit vpc / hub vpc) might be required. Specific outbound URLs can be whitelisted within Palo Alto to allow private subnets to access urls - e.g. for patching and update purposes.
See this post to understand a mature, best practices based HUB SPOKE network design on GCP.
Ingress Traffic Inspection versus East to West Traffic Inspection?
People may interchangeable use East-West and Ingress traffic flow.
Ingress flow can be east to west, but typically, INGRESS refers to Internet traffic coming into the VPC.
East to west refers to VPC to VPC traffic (e.g. Public VPC to Transit VPC OR Transit VPC to Security VPC). Think 'Within the Cloud Environment' when you hear East-West.
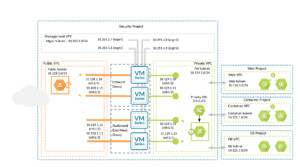
East West Traffic Inspection on GCP
Using a Shared Host VPC as a hub and several spokes as Service Projects, a potential design, with east to west traffic filtering might look like:
- Management VPC (for palo alto) needs a separate interface- and that means a separate VPC (A Compute instance CAN have multiple interfaces but they have to be in different VPCs).
- LEFT MOST A SINGLE (Regular) PROJECT with 3 VPCs - a Transit VPC (that is for vendor access and palo alto filters this traffic) and a separate HUB VPC (for future scalability).
- MIDDLE - A SHARED HOST VPC.
- RIGHT MOST - A Set of Service Projects and Service VPCs
What are cloud native options to custom appliances like Palo Alto?
GCP offers cloud armor and Cloud IDS.
- Google Cloud IDS - Like a Palo Alto - but has limited capabilities.
- Cloud Armor (WAF) - is mainly for perimeter security - no other boundaries are addressed.
- This is not possible in GCP, since the routing between subnets is automatic.
Summary
Traffic inspection is often REQUIRED and not an optional feature on a cloud network design. This post summarizes some of the common use cases on GCP and where Palo Alto may fit in.
Leave a Reply