Compute Engine Restrict Access – restrict service accounts in GCP
Two relevant roles to assign to IAM user - Compute Instance Admin and Service Account User.
roles/compute.instanceAdmin.v1, roles/iam.serviceAccountUser
Note the prefixes on these two. The instanceAdmin is related to the COMPUTE service, but the serviceAccountUser just says 'iam'. What does that mean? That means that this IAM user can use ANY service account within GCP. Including the default service account that is used for compute engine operations. The ACTUAL compute engine service account looks like an email address.
- Make sure you grant 'Compute Engine User' as a role to the IAM user. The actual service account they use (email address...@....) - is the default service account for compute engine.. As long as they are granted the Compute Engine User role, they should be able to use the instance - including log in.
- A 'compute Browser' Role --> That lets them see every compute instance on there. What if you ONLY wanted them to see their instance?
Restricting Access Scopes - restrict service accounts GCP
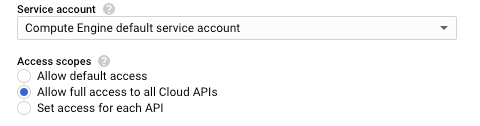
The only thing stopping the default service account from being able to utilize all of its permissions are the “access scopes” - assigned during the VM creation time.
This is a control that dictates which APIs the service account is able to access. So, if the service account is granted access to the Storage API in the IAM policy, the account still cannot access the Storage API if the access scopes do not include the Storage API. Here is an example the access scope options available in the GCP console:
Summary
Default compute engine Service accounts are far too permissive. Restrict access by using the tips in this post.
Need an experienced Cloud Professional to help out with your Public Cloud Strategy? Set up a time with Anuj Varma.
Leave a Reply